After successfully removing virus from Windows 10 system, the journey doesn’t end there. It’s imperative to take proactive steps to secure and optimize your device fully. Let’s know together.

Table of Contents
Toggle1. Things You Must Do After Removing Virus from Windows 10
To have a clean PC or Windows you must do some steps to ensure that your device is safe to use and they are as follows.
2. Perform a Full System Scan
Once you’ve eliminated the virus, the first step is to conduct a comprehensive system scan. This ensures that no remnants or hidden threats persist on your Windows 10 system. Utilize reliable antivirus software, running a deep scan to identify and eliminate any lingering malware. This step provides a crucial assurance that your system is clean and free from potential threats.
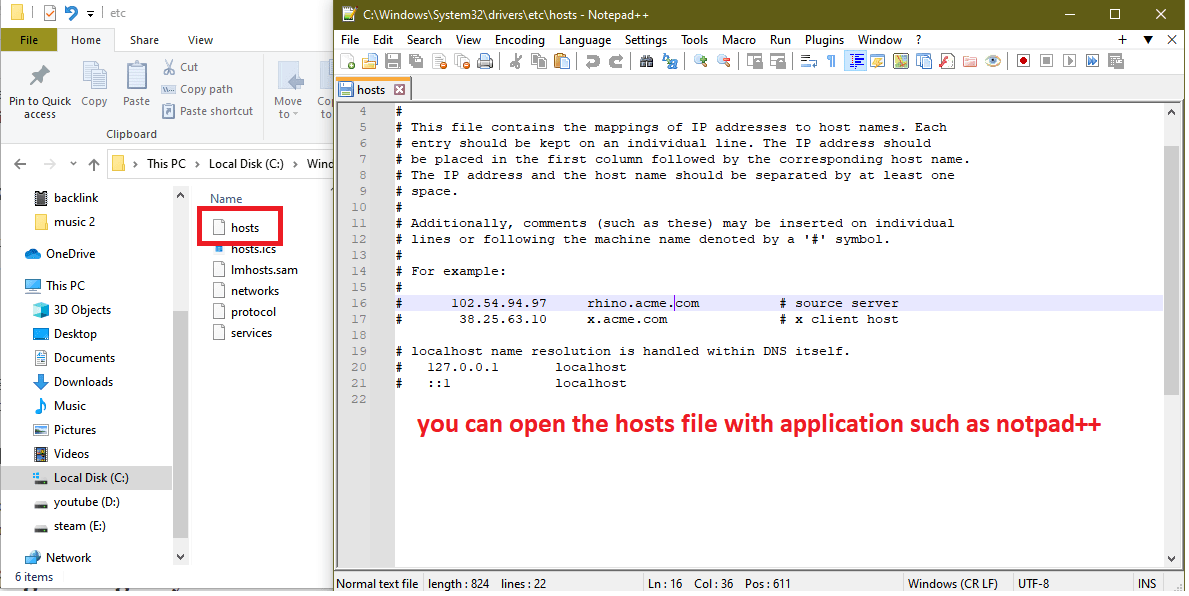
3. Checking the Hosts file has not been tampered with
Typically, viruses are programmed to take control of the Hosts file, responsible for mapping domain names to IP addresses. This manipulation is often aimed at thwarting user connections to Microsoft servers or obstructing access to antivirus manufacturer websites, preventing the virus’s removal. Therefore, it is crucial to initially verify the integrity of the Hosts file to ensure it has not been compromised, You can follow these steps to check:
- First, go to this directory C:\Windows\System32\drivers\etc
- Click on the hosts file and select Open with Notepad or as i use Notepad++.
- Checking the last lines of the file are genuine names are added such as com or Microsoft.com
- Delete strange addresses and save files make sure to log in as an administrator.
4. Update Your Operating System and Software
Keeping your operating system and installed software up to date is paramount for security. Regular updates include patches and fixes for known vulnerabilities, strengthening your system’s defenses against potential threats. Enable automatic updates to ensure a seamless and consistent approach to maintaining the security of your Windows 10 device.
5. Cleaning the registry values from malicious software
Malicious software may also modify Windows registry keys, commonly known as Registry using the Registry Editor tool. This allows them to regain access to the operating system’s settings and data even after being removed from the device. Therefore, after removing malicious software, it is essential to ensure that it hasn’t altered or added new keys to the registry to prevent further infections. Verify this by following these steps.
- Open Registry Editor in administrator mode by pressing Win + S, typing regedit in the search bar, and selecting Run as an administrator in the results. Once the tool window appears, press Ctrl + F to open the registry search window. In the Find What field, enter the name of the recently removed malicious program or virus. Press Enter and wait for the search to complete.
- If any suspicious keys with unfamiliar names or associations with the virus or malicious program you removed are found, right-click on them, and select Delete to remove them from the registry.
Exercise caution during these steps to avoid randomly deleting registry keys, as haphazard deletions may lead to the collapse and malfunction of the operating system. It is recommended to create a backup of the registry before making any modifications or removals.
6. Change Passwords Immediately
Security breaches often involve compromised passwords. In the aftermath of a virus removal, it’s crucial to change all your passwords. This includes passwords for your operating system, email accounts, and any online platforms you use. Opt for strong, unique passwords that combine letters, numbers, and symbols for enhanced security. This simple yet effective step significantly reduces the risk of unauthorized access to your accounts.
7. Create a System to Restore Point
Before making any significant changes or updates to your system, create a system restore point. This precautionary measure allows you to revert to a stable system state in case of unforeseen issues. It acts as a safety net, providing you with the ability to undo changes and restore your Windows 10 system to a previously known good state.
8. Install a trusted Antivirus Program
Choosing a reputable antivirus program such as Kaspersky is crucial for ongoing protection against evolving threats. Install a reliable antivirus program on your Windows 10 device and regularly update its virus definitions. Additionally, schedule periodic scans to ensure proactive detection and removal of potential malware. Investing in a robust antivirus solution is an essential aspect of maintaining a secure computing environment.
9. To ensure that the web browser is not compromised
Some users overlook that viruses and malicious software may compromise web browsers, making changes even after removal. These alterations can enable the re-entry of malicious software when using the same web browser. After removing malware, ensure your web browser is not compromised.
Verify by opening your usual internet browsing program and checking for any new unknown add-ons recently added. Confirm no new search engine has been set up without your knowledge. Check for suspicious and unknown web pages added to your browser’s startup settings. Finally, revert any changes made by the malware, resetting all web browser settings to their original values or their previous state before the malware infiltrates your device.
10. Optimize System Performance
After eliminating a virus, take steps to optimize your system’s performance. Disable unnecessary startup programs, clear temporary files, and defragment your hard drive. These actions contribute to a smoother and faster computing experience. By optimizing your system, you not only enhance its performance but also create a more resilient defense against potential future threats.
11. Educate Yourself on Phishing Awareness
Phishing attacks are prevalent and can pose significant risks to your cybersecurity. Take the time to educate yourself on common phishing tactics and stay vigilant against suspicious emails and links. Being aware of potential threats adds an extra layer of defense, reducing the likelihood of falling victim to phishing scams.
12. Enable Firewall Protection
Activate the built-in Windows Firewall or install a reputable third-party firewall to enhance your system’s defense mechanisms. Firewalls oversee and regulate both inbound and outbound network traffic, thwarting unauthorized access and potential security breaches. Ensuring your firewall protection is active provides an additional barrier against external threats.
13. Secure Your Wi-Fi Network
A secure Wi-Fi network is essential for safeguarding your Windows 10 device. Update your Wi-Fi password regularly and use WPA3 encryption for enhanced security. By securing your Wi-Fi network, you minimize the risk of unauthorized access and potential threats originating from unsecured networks.
14. Disable Suspicious Processes and Services
After removing viruses and malicious software, the recommended step is to disable all services and processes added by the malware to prevent re-access. Exercise caution during this process, only disabling identified disruptive processes, as improper termination may lead to Windows instability.
To terminate malicious processes, right-click Start, choose Task Manager go to Startup, and disable suspicious programs. As a confirmation step, press Win + S search for System Configuration press Enter. In the appearing window, navigate to Services check Hide all Microsoft Services unmark services linked to the malware, and click OK to save changes.
15. Back-Up Important Data
Establishing a routine backup for your critical data is a crucial step in post-virus removal precautions. Use external hard drives or reliable cloud services to store important files securely. In the event of a future security incident, having a backup ensures that you won’t lose essential information.
16. Monitor System Activity
Vigilance is key in maintaining a secure system. Regularly monitor your system’s activity by checking task manager reports and network activity. Look out for any unusual or suspicious behavior, as early detection is instrumental in preventing potential threats from causing harm to your Windows 10 device.
17. Seek Professional Assistance if Necessary
If you find yourself uncertain about any aspect of your system’s security, don’t hesitate to seek professional assistance. Consulting with cybersecurity experts can provide personalized recommendations tailored to your specific situation. Their expertise ensures that your Windows 10 device receives thorough and effective protection against potential threats.
18. Stay Informed About the Latest Threats
Cybersecurity is a constantly evolving field, with new threats emerging regularly. Stay informed by subscribing to reputable security blogs such as the hacker news or Krebs on Security and newsletters. This ensures that you’re up to date on the latest cybersecurity threats and best practices, allowing you to adapt your security measures accordingly.
19. Enhance Email Security Settings
Email accounts are often targeted in cyberattacks. Enhance your email security settings by adjusting spam filters and enabling two-factor authentication. These measures significantly reduce the risk of falling victim to email-based threats, contributing to your overall system security.
20. Evaluate and Enhance Browser Security
Your web browser is a gateway to the online world, making its security crucial. Evaluate and enhance your browser’s security settings by adjusting privacy settings, disabling unnecessary extensions, and keeping the browser updated. A secure browser adds an extra layer of protection to your overall online safety.
FAQs

Q1 How often should I run a full system scan after removing a virus from Windows 10?
It’s recommended to run a full system scan at least once a week to ensure ongoing security. Adjust the frequency based on your online activities and the sensitivity of the information on your system.
Q2 Can I rely solely on Windows Defender for antivirus protection?
While Windows Defender provides baseline protection, investing in a dedicated antivirus program from a reputable vendor offers additional features and a higher level of security against a broader range of threats.
Q3 Is it necessary to change all my passwords after removing a virus?
Yes, changing all your passwords is a crucial step in preventing unauthorized access. This includes passwords for your operating system, email accounts, and any online platforms to which you have access.
Q4 What should I do if I detect unusual system activity after removing a virus?
If you notice unusual system activity, disconnect from the internet immediately and run a thorough antivirus scan. If issues persist, seek professional assistance to ensure a comprehensive analysis and resolution.
Q5 What are the best ways to stay informed about the latest cybersecurity threats?
Stay informed by subscribing to reputable security blogs, and newsletters, and following cybersecurity experts on social media. Regularly check for updates from reliable sources to stay ahead of emerging threats.
Q6 Is it safe to use public Wi-Fi after removing a virus from my Windows 10 device?
Exercise caution when using public Wi-Fi. Ensure your connection is secure, use a virtual private network (VPN), and avoid accessing sensitive information while connected to public networks.
Conclusion
Securing your Windows 10 system after removing a virus is a comprehensive process that requires diligence and proactive measures. By following the outlined steps and incorporating best practices, you can fortify your device against potential threats. Stay informed, stay vigilant, and prioritize the ongoing security of your Windows 10 system.
Finally, I hope my article added some valuable information to you. IF you have some questions? Let me know in the comments below. I’ll try my best to answer them




